Ingress Vs Egress – What’s The Difference
We are reader gimbaled and whitethorn earn a commission when you grease one's palms through golf links on our site. Learn more
Ingress vs egress: there seems to be a never-ending debate about these terms. They're genial of archaic and their meaningful seems to be different in contrary situations.
Now, we'll behave our best to try to shed some light on this mystery. We don't want to get into a unemotional debate, though. Our only goal is to do our superior to explain these terms you bet they are typically used in the context of networking. But evening that, A you're about to see, can tend to be rather confusing.
Ingress Vs Egress
- We'll begin by shaping these two terms, first linguistically and then in the specific context of computer networks.
- We'll then explicate how their meaning can buoy vary founded on one's point of view of based on the scope that we'Re contemplating. The same emersion traffic in cardinal situation can become ingress traffic in other.
- Next, we'll talk about monitoring incoming and egress traffic and introduce close to of the best tools you can economic consumption for that purpose. But wait! There's more.
- We'll also discuss egress in the proper context of data security and introduce few the best practices to protect yourself against data go forth.
- And, keeping our good habits, we'll review approximately of the best SIEM tools that you bum use to detect unwanted data egress.
Defining Ingress And Come out
Linguistically speaking, defining either of those words could hardly be easier (pun intentional). Army of the Pure's hear what the Merriam-Webster dictionary has to say about it.
- It simply and plainly (almost tediously) defines ingress as "the act of ingress". Simple enough, no?
- And come forth is not much more complicated As the same source defines it arsenic "the natural action of expiration or coming come out of the closet".
Here again, a beautiful simple definition. If you care to check other sources, you'll find a decided consensus. Ingress is getting in while egress is getting exterior.
In The Context Of Network Dealings
But this blog post is not virtually linguistics, it's about electronic network administration. And this is were entry and egress can get a bit Sir Thomas More unclear. It's still the indistinguishable, though and information technology has to do with data entering and departure a network, a device or an interface. As yet, nothing complicated. Where it gets tricky, though, is when people don't agree on what's in and what's out. You see, sometimes the ins of one are the outs of another.
It All Depends On Your Pointedness Of View
Entrance OR egress, when referring to network traffic, has to do with how you catch things, information technology depends happening your target of view. In most other situations, in is in and impermissible is out; there's nothing confusing virtually that. This is, however, not so much the case with networks. Let's try to elucidate that using a fewer concrete examples.
Our first example is that of an Internet gateway. It could be a router, a placeholder server or a firewall, that doesn't matter. Information technology is the device that sits between your local network and the Internet. Therein lawsuit, I think everyone would agree that the Cyberspace is considered as being the outside and the local network, the inside.
So, traffic climax FROM the Internet TO the local network would Be ingress traffic and traffic FROM the local network TO the Internet would Be egress traffic. So far, it's still fiddle-shaped.
Merely if you look at things from a network interface stand, things get different. In the previous exercise, if you deal dealings on the LAN interface, traffic going towards the Net is straight off ingress traffic as it is entering the gateway. Too, traffic going toward the local meshing is non egress dealings as information technology is exiting the gateway.
To summarise, differentiating incoming and egress traffic requires that we all agree on what we'Re talking about.
As we saw, ingress traffic in one context can be egress dealings in a different one. Our best suggestion would be to either avoid using these terms altogether or to clear state their utilization context every metre you use them. That way, you'll avoid some confusion.
Monitoring Egression And Ingress Dealings
Immediately that we're familiar with the terminology, let's get a load at monitoring ingress and egress traffic.
Typically, this is done using special software called network monitoring operating room bandwidth monitoring tools. These tools use the Simple Network Direction Protocol (SNMP) to read interface counters from network-connected equipment. These counters simply tally the number of bytes in and out of each network interface.
Remark that monitoring tools rarely use ingress and egress and usually concern to traffic in and out of an user interface. Information technology is adequate you, if you so desire, to settle which is ingress and which is egress traffic, again depending on the specific context.
A couple of Tools We'd Recommend
There are many bandwidth or network monitoring tools available. Probably too many and pick the best one—or even vindicatory a intellectual one—can embody a take exception. We've proven many of the open tools and came up with this lean of a few of the very second-best bandwidth monitoring tools you can find.
1. SolarWinds Network Operation Monitor (Loose Trial run)
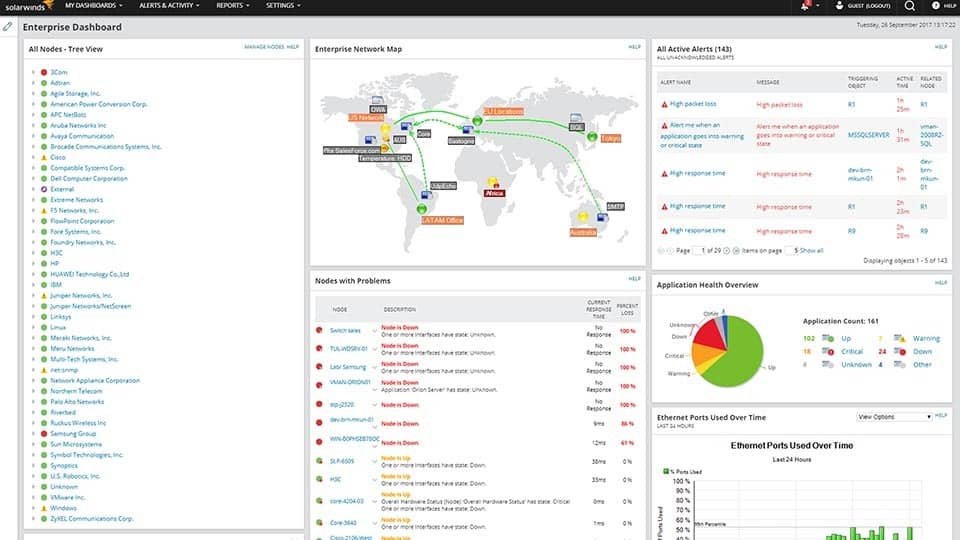
SolarWinds is one of the very best makers of web administration tools. The company's flagship product is called the SolarWinds Network Performance Monitor, or NPM. It is a very complete net monitoring solvent that features a user-cozy graphic interface that administrators posterior use to supervise devices and to configure the instrument.
The system uses SNMP to inquiry devices and display their interfaces' utilization as well as other useful metrics on a graphical dashboard.
In add-on to this dashboard, various built-in reports can be generated either on-demand surgery supported a scheduled execution. And if the built-in reports don't give you the information you need, they give the sack Be customized at will.
The package likewise includes a few useful tools such as the ability to display a visual rendition of the nitpicking patch between any two points of the network. This tool is extremely scalable and it will suit whatsoever web from the smallest to large networks with thousands of devices bedcover over multiple sites.
- FREE TRIAL: SolarWinds Network Performance Monitoring device
- Formalized download data link: https://web.solarwinds.com/network-performance-monitor/enrolment
The SolarWinds Network Performance Monitor's alerting system is another place where the product shines. As its reports, information technology is customizable if needed but it can also be victimised out-of-the-corner with minimal configuration. The alert engine is smart plenty not to direct notifications for "unimportant" events in the middle of the night or to send hundreds of notifications for as many unresponsive devices when the main issue is a down router operating theatre network switch upriver.
Pricing for the SolarWinds Network Performance Monitor starts at just low $3 000 and goes up according to the enumerate of devices to proctor.
The pricing structure is actually sooner complex and you should contact the SolarWinds gross revenue team for a detailed quote.
If you prefer to try the product before buying it, a free 30-day trial version is available for download from the SolarWinds website.
2. ManageEngine OpManager
ManageEngine is another well-known publisher of mesh management tools.
The ManageEngine OpManager is a complete management resolution that will plow bad some any monitoring task you can throw at it.
The tool runs on either Windows or Linux and is loaded with large features. Among others, there is an auto-discovery feature that can map your network, giving you a uniquely bespoken dashboard.
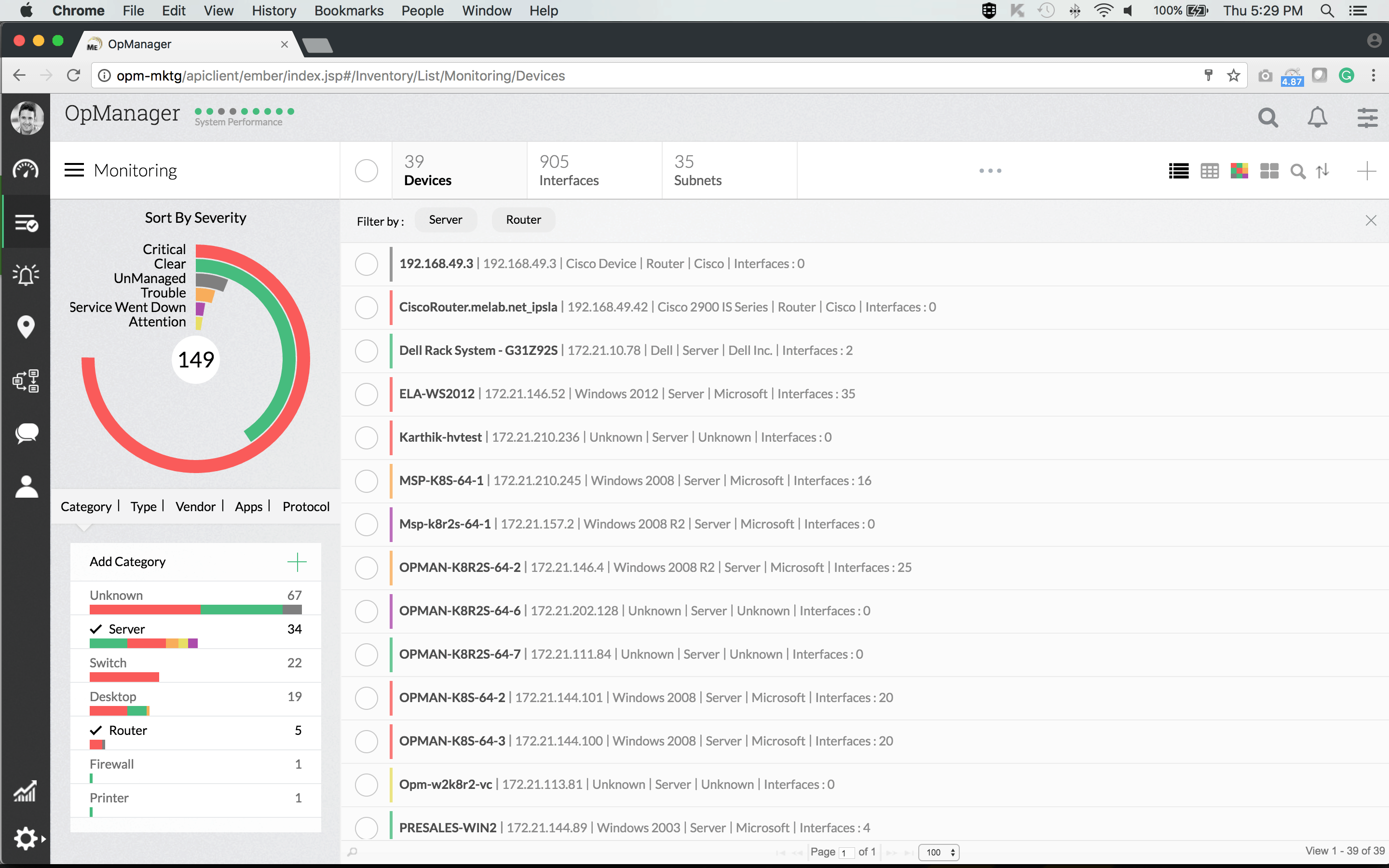
The ManageEngine OpManager's dashboard is super wanton to employ and navigate, thanks to its exercise-down functionality. And if you are into mobile apps, there are apps for tablets and smartphones allowing you to access the tool from anywhere. This is an overall very polished and professional product.
Alerting is even as good in OpManager as are all its strange components. There is a full complement of door-based alerts that volition help detect, distinguish, and troubleshoot network issues. Two-fold thresholds with different notifications can be set for all network performance metrics.
If you neediness to try the ware earlier buying, a free version is available. Although it is a truly free version rather than a time-limited trial run, it has just about limitations such arsenic letting you monitor atomic number 102 to a greater extent than ten devices.
This is low for all but the smallest of networks. For big networks, you stool pick out between the Essential or the Enterprise plans. The first will allow you monitor up to 1,000 nodes piece the other goes capable 10,000.
- FREE TRIAL: ManageEngine OpManager
- Official download link : https://web.manageengine.com/network-monitoring-msp/download.html
Pricing entropy is useable by contacting ManageEngine's sales.
3. PRTG Network Monitor
The PRTG Network Supervise, which we'll just refer to arsenic PRTG, is other great monitoring system. Its publisher claims that this tool can monitor lizard all systems, devices, traffic, and applications of your IT base. It is an all-inclusive package that does not swear on external modules operating theater add-ons that need to be downloaded and installed. Because of its integrated nature, it is quicker and easier to install than most other network monitoring tools. You lav choose between a some different exploiter interfaces much A a Windows enterprise console, an Ajax-supported web interface, and mobile apps for Android and iOS.
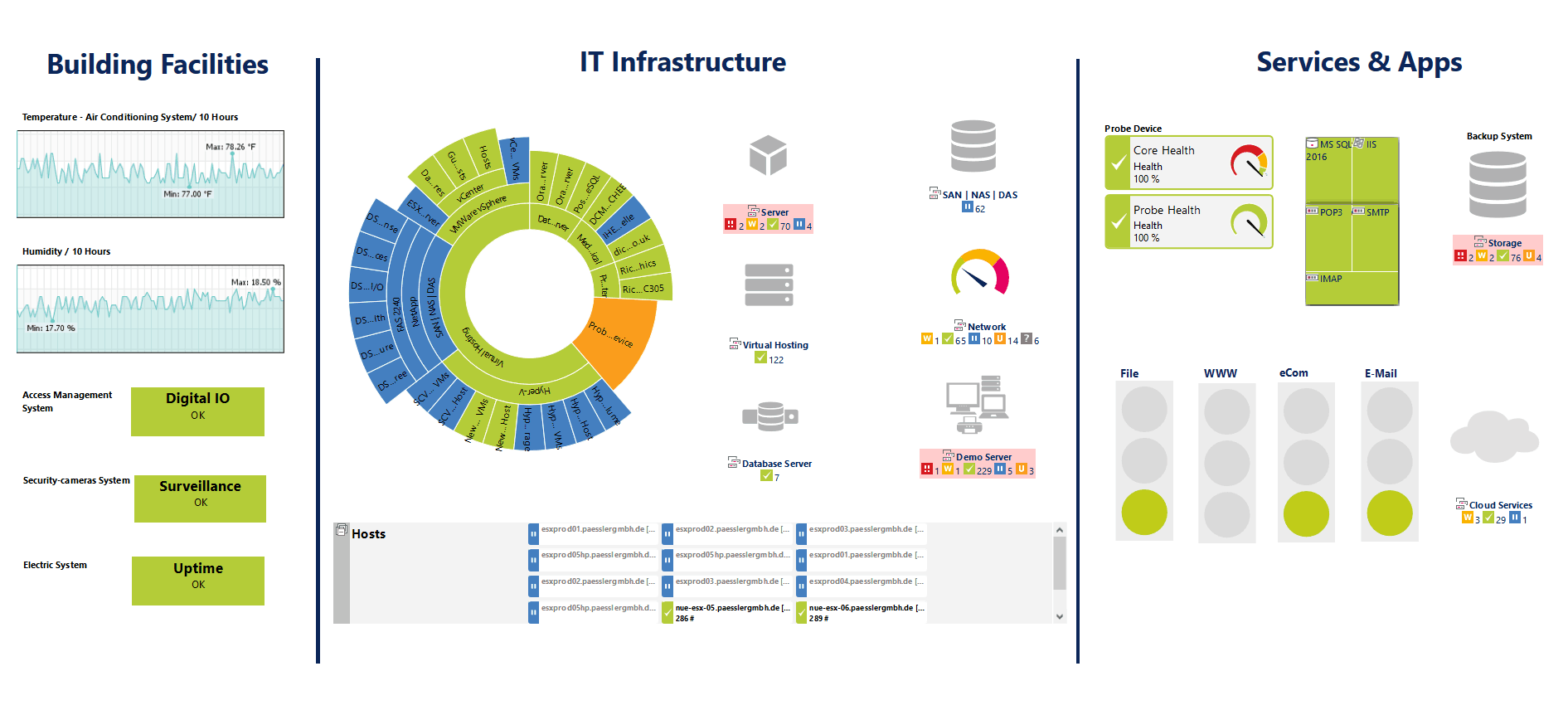
The PRTG Web Monitor is different from most other monitoring tools in this it is sensor-based. Various monitoring features can be added to the tool simply by configuring extra sensors. They are like plugins except that they are not external modules but are, instead, included with the product. PRTG includes o'er 200 such sensors that cover different monitoring necessarily. For network carrying into action metrics, the QoS sensor and the Advanced PING Sensing element set aside you to monitor latency and jitter while the standard SNMP sensor will let you monitor throughput.
The PRTG pricing social system is pretty simple. There's a free version which is full-conspicuous but will limit your monitoring power to 100 sensors. On that point's also a 30-day trial run translation which is unlimited merely will turn back back to the dislodge translation once the trial historical period is over. If you want to retain monitoring Sir Thomas More than 100 sensors beyond the test period, you'll motive to purchase a license. Their price varies according to the number of sensors from $1 600 for 500 sensors to $14 500 for infinite sensors. Each monitored parameter counts arsenic one sensor. E.g., monitoring bandwidth on for each one port of a 48-port switch bequeath matter to American Samoa 48 sensors.
Egress In The Linguistic context Of Security
Thither is some other use for the term egress among network and system administrators that is specific to the context of information security. It refers to data leaving an organization's local anesthetic network. Outgoing email messages, cloud uploads, or files being sick to auxiliary storage are simple examples of data egress. It is a normal part of network activity, but it can stick a threat to organizations when sensitive information is leaked to unauthorized recipients, either unknowingly or maliciously.
Threats Involving Information Egress
Sensitive, proprietary, OR well monetizable information is often targeted by cybercriminals of all kinds. The release of sensitive or proprietary information to the public or to competing organizations is a existent concern for enterprises, governments, and organizations of all kinds. Threat actors may prove to steal sensitive data through the very methods more employees role every Clarence Day, such as email, USB, or cloud uploads.
Go-to-meeting Practices For Preventing Unwanted Data Egress
There's a lot you can do to protect your brass against unauthorized data egress but a couple of of them are particularly important. Let's make a deal two of the bare essentials that you must do.
Make over an acceptable use and data egress traffic enforcement policy
Include stakeholders to define your acceptable use policy. The policy should glucinium real careful and protect your company's resources. It could, for instance, include a list of approved Internet-in hand services and guidelines for accessing and handling sensitive information. And don't draw a blank that it is one thing to make such policies only you also need to communicate them to users and make sure they interpret them.
Implement firewall rules to block egress to spiteful or unauthorized destinations
A network firewall is only united of several lines of defense against threats. It is a good terminus a quo where you can guarantee that data egress does not hap without unequivocal permission.
SIEM – To Help Forestall Data Issue
No matter what you manage, monitoring cadaver one of the best ways to protect against data emergence. Whenever data leakage happens, you want to know about information technology right away and then you ass influence it. This is where Security system Information and Event Management (SIEM) tools bathroom aid.
Concretely, a SIEM system does non allow for some hard tribute. Its direct purport is to make the life of network and security administrators like you easier. What a typical SIEM system really does is accumulate information from various protection and spotting systems, correlate all this information assembling related events, and react to meaningful events in various ways. Most of the time, SIEM tools also include some form of reporting and/Oregon dashboards.
Approximately Of The Exceed SIEM Tools
To give you an idea of what's uncommitted and to help you woof the correctly SIEM tool for your needs, we've assembled this list of several of the top SIEM tools.
1. SolarWinds Security measur Event Manager (FREE TRIAL)
The selfsame SolarWinds that brought us the Network Monitor reviewed above also has an offering for Security measures Information and Event Management. In fact, it is one of the identical best SIEM tools available. It might not be American Samoa full-featured as another tools but what it does, it does fine and it has all the required functionality. The tool is called the SolarWinds Security department Result Manager (SEM). Information technology is best described as an entry-level SIEM system but it's likely one of the most competitive entry-level systems along the food market. The SolarWinds SEM has everything you can carry from a SIEM system, including excellent lumber direction and correlational statistics features that can facilitate detect unauthorized data emersion and an impressive reporting railway locomotive.
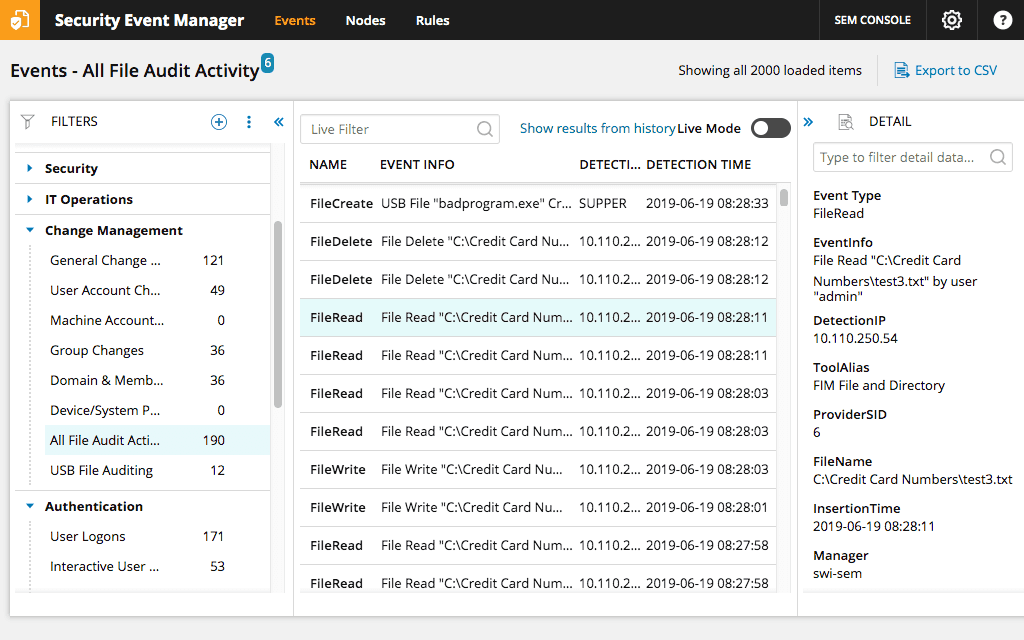
FREE TRIAL: SolarWinds Certificate Issue Manager
Official Download Link: https://www.solarwinds.com/security-outcome-managing director/readjustment
As for the tool's event response features, as expected from SolarWinds, they depart nothing to be desired. The elaborated real-clock answer system testament actively respond to every menace. And since it's based connected behaviour rather than a signature, you're protected against unknown or future threats. The tool's dashboard is possibly one of its best assets. With a simple project, you'll have no trouble speedily identifying anomalies. Starting at around $4 500, the tool is more than affordable. And if you want to try IT first, a free fully functional 30-day test version is available for download.
Authorized Download Link: https://WWW.solarwinds.com/security-event-manager/registration
2. Splunk Enterprise Security
Possibly unrivalled of the about popular SIEM system, Splunk Enterprise Security–or simply Splunk E, Eastern Samoa it is often known as–is famous for its analytic capabilities. Splunk ES monitors your system's data in real time, looking for vulnerabilities and signs of abnormal activity. The system uses Splunk's own Adaptive Response Framing (ARF) which integrates with equipment from more than 55 security measures vendors. The ARF performs machine-controlled response, letting you quickly pull in the upper hand. Add to that a simple and tidy user port and you induce a winning solution. Other interesting features include the "Notables" function which shows drug user-customizable alerts and the "Asset Police detective" for flagging malicious activities and preventing further problems.
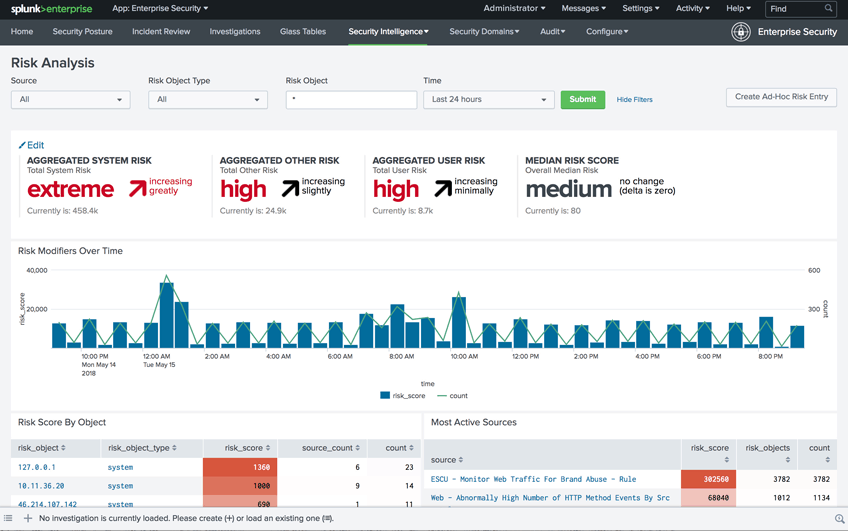
Splunk ES is an endeavor-grade cartesian product and, per se, it comes with an enterprise-shrew-sized terms tag. You hind end't, unluckily, induce much pricing information from Splunk's website and you'll call for to contact the gross revenue department to get a quote. Despite its price, this is a important product and you might want to reach Splunk to take reward of an available free trial.
3. NetWitness
For the past few years, NetWitness has focused on products supporting "deep, period network situational awareness and agile electronic network reply". After being purchased by EMC which then merged with Dell, the Netwitness business is now part of the RSA branch of the corporation. And this is good word as RSA has an excellent reputation in security.
NetWitness is ideal for organizations seeking a complete network analytics solution. The tool incorporates info about your business enterprise which helps prioritize alerts. Accordant to RSA, the system "collects information across more capture points, computing platforms, and threat intelligence sources than other SIEM solutions". In that respect's also advanced threat detection which combines activity analysis, data science techniques, and threat intelligence. And finally, the advanced reception organisation boasts orchestration and automation capabilities to help eradicate threats before they impact your business.
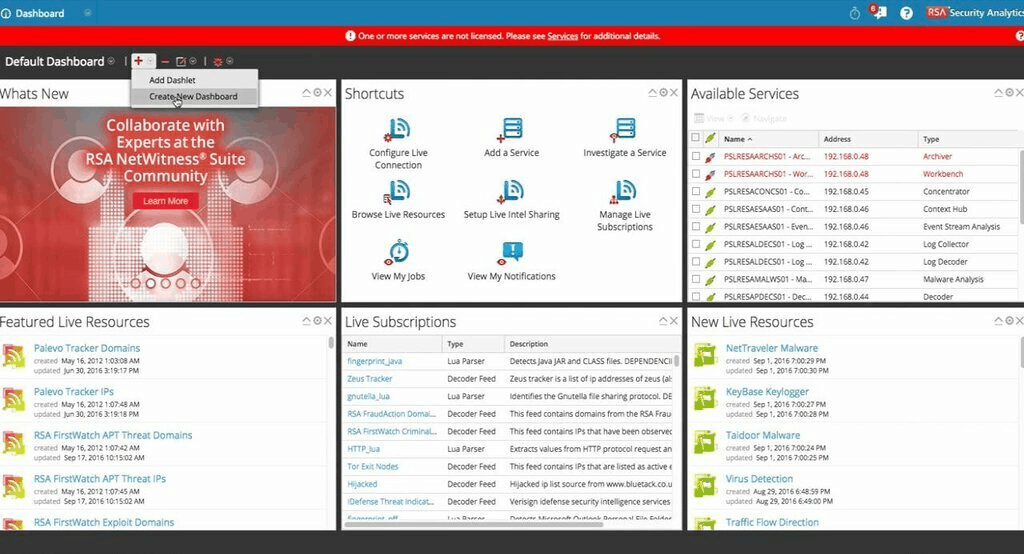
One of the main drawbacks of NetWitness is that information technology's non the easiest to set up and use. However, in that respect is ample documentation getable which can help you with setting up and using the product. This is another enterprise-grade product and, equally it is often the case with such products, you'll require to contact gross revenue to get pricing information.
Ingress Vs Egress – What's The Difference
Source: https://www.addictivetips.com/net-admin/ingress-vs-egress/
Posting Komentar untuk "Ingress Vs Egress – What’s The Difference"